The Model Context Protocol arrived like a lightning bolt, unifying how AI agents access data and systems. Now it's being joined by A2A, ACP, and a growing ecosystem of protocols, each addressing different dimensions of agent operations.
This is progress. But here's what enterprises are discovering: protocols are just the pipes. And pipes don't understand what flows through them.
The Evolution Beyond Protocol Gateways
Walk into any enterprise today, and you'll hear CISOs asking: "How do we govern our AI agents?"
The natural first answer: "Start with protocol gateways."
It's a logical step. Protocols like MCP are how agents connect. Gate the protocols, gate the agents. Simple.
And it works to a point. Protocol gateways handle what they're designed for: transport-layer control. They're essential infrastructure.
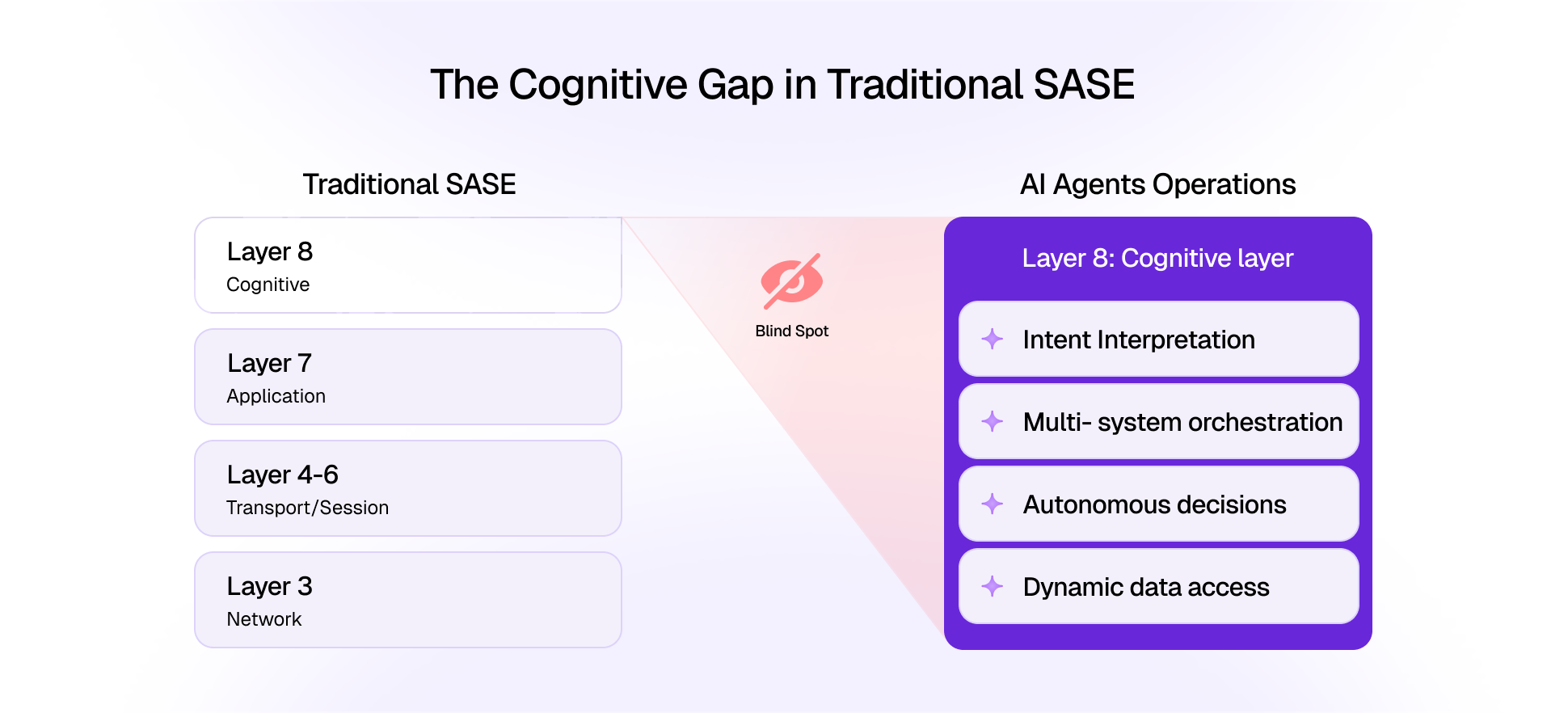
But they're not sufficient. Because protocol gateways are transport-layer solutions to a cognitive-layer challenge.
They see connections. They don't see context.
They monitor traffic. They don't understand intent.
They control access. They don't govern behavior.
That's not a flaw. That's just what they are: necessary checkpoints in a governance stack that needs much more.
What Enterprises Actually Need
Agent governance isn't a protocol problem. It's a data and behavior problem.
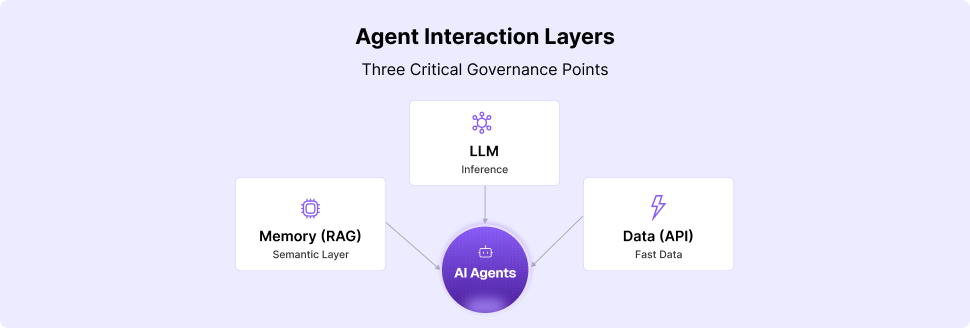
When an AI agent accesses your systems, three things matter:
- What data is it touching? Is it classified? Who owns it? Where did it come from? What policies apply?
- How is it reasoning? Is it invoking inference responsibly? Are there hallucination risks? Is the model behavior aligned with enterprise policy?
- What memory is it building? What's being embedded into RAG? What knowledge is being retrieved? Is the semantic layer governed?
MCP-only gateways answer none of these questions. They're protocol enforcers in a world that needs cognitive governance.
The Multi-Protocol Reality
The agent ecosystem isn't standing still.
MCP laid important groundwork for agent connectivity. Now new protocols are emerging to handle what MCP doesn't:
- Agent-to-Agent A2A for multi-agent orchestration
- Agent Calling Protocol ACP for structured interactions
- And more on the horizon, each addressing different operational needs
This is healthy evolution. The ecosystem is maturing, getting more sophisticated, more capable.
But it creates a challenge: protocol-specific gateways become point solutions in a multi-protocol world.
They're Layer 4 tools in an ecosystem that demands Layer 8 governance, the cognitive layer where agents access data, invoke reasoning, and build memory.
Enterprises need governance that transcends any single protocol. Not because protocols don't matter, but because the protocols will keep evolving while the governance requirements remain constant.
Data-First, Agent-Aware, Protocol-Agnostic
At Daxa, we took a different path.
While others built MCP-only solutions, we asked a harder question: What if we governed agents where it actually matters, at the intersection of data, inference, and memory?
We support MCP today. We secure the pipe, diving deep into protocol-specific issues that matter for strong transport-layer security. But our platform was designed protocol-agnostic from day one, ready for A2A, ACP, and whatever protocols emerge next.
That future-proof architecture led us to three foundational pillars:
1. Safe Agent: Multi-Protocol Operations
We support MCP today, securing protocol-specific vulnerabilities at the transport layer. But agents don't live in one protocol. They orchestrate across MCP, A2A, ACP, and protocols that don't even exist yet. Our governance layer is protocol-agnostic by design, built to adapt as the ecosystem evolves, not locked to any single pipe.
2. Safe Infer: LLM Invocation Governance
Every agent decision flows through an inference call. That's where hallucinations happen. That's where bias creeps in. That's where model behavior either aligns with policy or doesn't. We govern the reasoning layer, not just the transport layer.
3. Safe RAG: Semantic Memory Control
RAG isn't just retrieval. It's how agents remember, learn, and build context over time. Without governance here, you're flying blind on what knowledge your agents are building. We classify, lineage track, and policy enforce at the memory layer because that's where enterprise risk actually lives.
Together, these three pillars create something MCP gateways fundamentally can't: agent and data governance that evolves with the ecosystem.
The Real Question CISOs Should Ask
It's not "Do we have an MCP gateway?"
It's "Do we understand what our agents are doing with our data, how they're reasoning through our systems, and what memory they're building over time?"
If the answer is no, you don't have an agent security problem. You have a visibility and governance gap that no protocol-layer tool can solve.
The Path Forward
Protocol gateways aren't the wrong answer. They're one layer of the answer.
They handle transport security. That matters. But enterprises racing toward autonomous operations need the full stack: protocol control plus cognitive governance that understands:
- The data agents touch
- The inference agents invoke
- The memory agents build
Across every protocol, MCP and whatever emerges next. At every decision point. With full lineage, classification, and policy enforcement.
That's not just a gateway. That's a governance platform built for an evolving ecosystem.
The choice is clear: Build point solutions for each protocol as it emerges, or build governance that evolves with the ecosystem.
At Daxa, we chose the latter. We support MCP today, securing the pipe and addressing protocol-specific issues. But we built Safe Agent to be protocol-agnostic from the ground up, ready for A2A, ACP, and whatever the community develops next.
Because the protocols will change. The pipes will multiply. But the core governance challenge, controlling what agents access, how they reason, and what they remember, that's permanent.
The question isn't whether the agent ecosystem will evolve. It's whether your governance can keep pace.
Interested in how Daxa's agent and data governance works across Safe Agent, Safe Infer, and Safe RAG? Let's talk about what production-ready autonomous security actually looks like.