Secure Retrieval-Augmented Generation (RAG) in Enterprise Environments
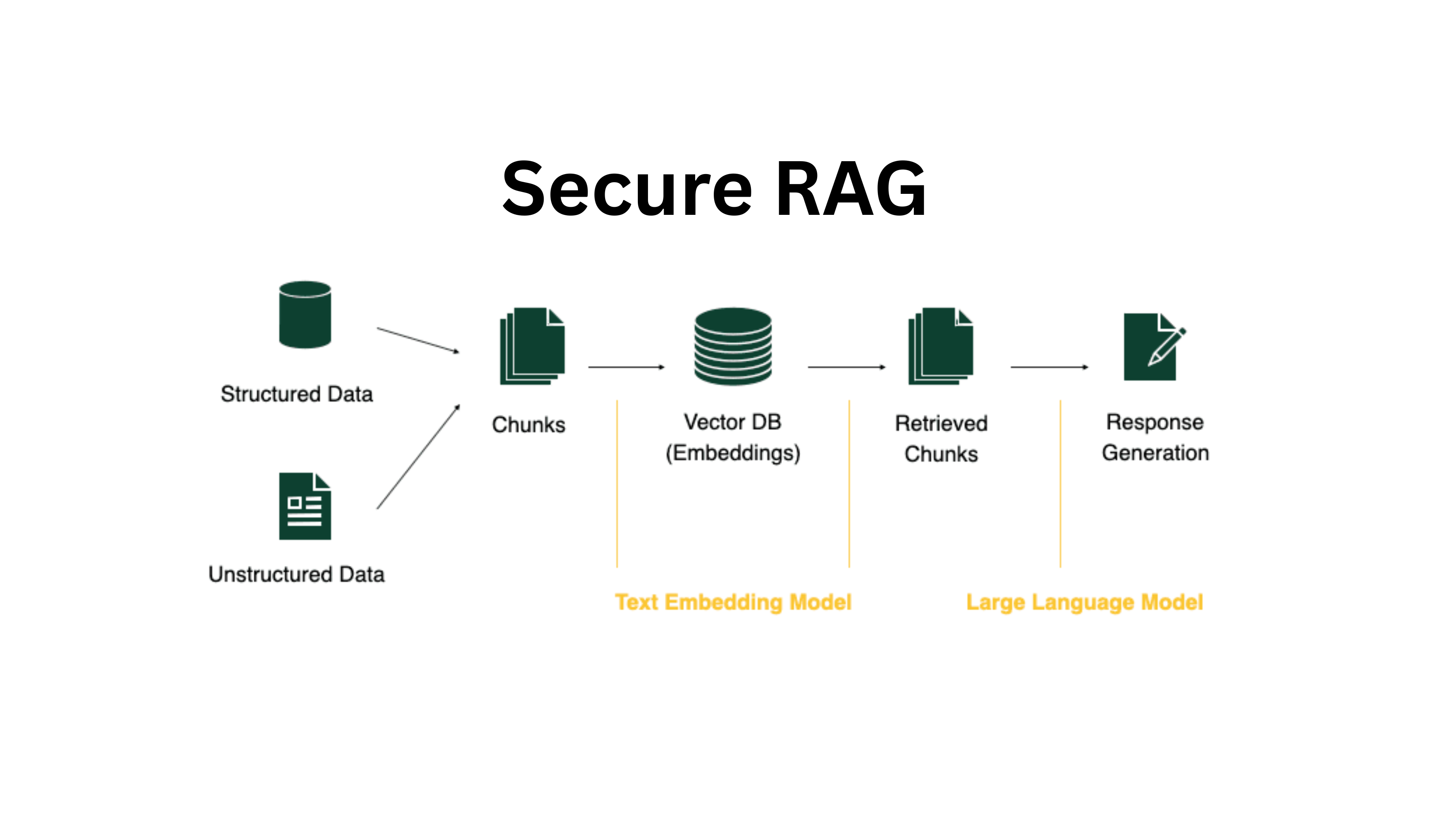
Retrieval-Augmented Generation (RAG) is accelerating enterprise AI adoption by combining large language models (LLMs) with internal knowledge bases to deliver real-time, data-grounded responses. This powerful architecture introduces significant risks, including sensitive data exposure, regulatory violations, and adversarial prompt manipulation, that must be proactively addressed. Security must be embedded by design to realize RAG's value without undermining trust or compliance posture.
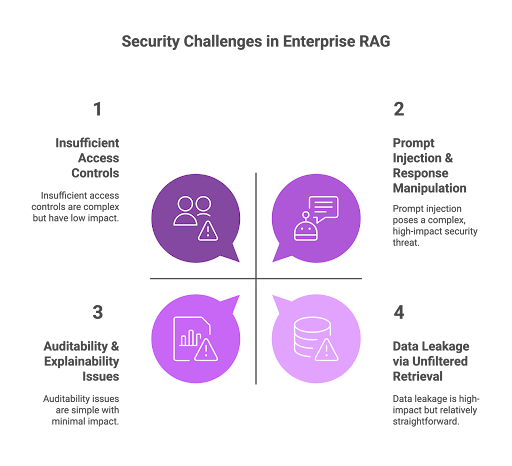
Security Challenges in Enterprise RAG
Prompt Injection & Response Manipulation
Adversarial content embedded in user input or retrievable documents can hijack model responses, bypassing access controls and policies. Prompt injection attacks are a heightened risk in RAG due to the close coupling of user queries and retrieved enterprise data.
Data Leakage via Unfiltered Retrieval
Without strict controls, retrieval pipelines may surface internal-only or sensitive data, even in public-facing applications. Documented cases highlight how improperly scoped retrieval can expose PII or regulated content under GDPR and HIPAA.
Insufficient Access Controls
Traditional RBAC often lacks the granularity for RAG. Implementing attribute-based (ABAC) or relationship-based access controls creates dynamic, context-sensitive policies for both queries and content.
Auditability & Explainability Issues
Failing to rigorously log all queries, retrievals, filtering, and generation steps undermines compliance and incident forensics, resulting in lost trust and failed audits.
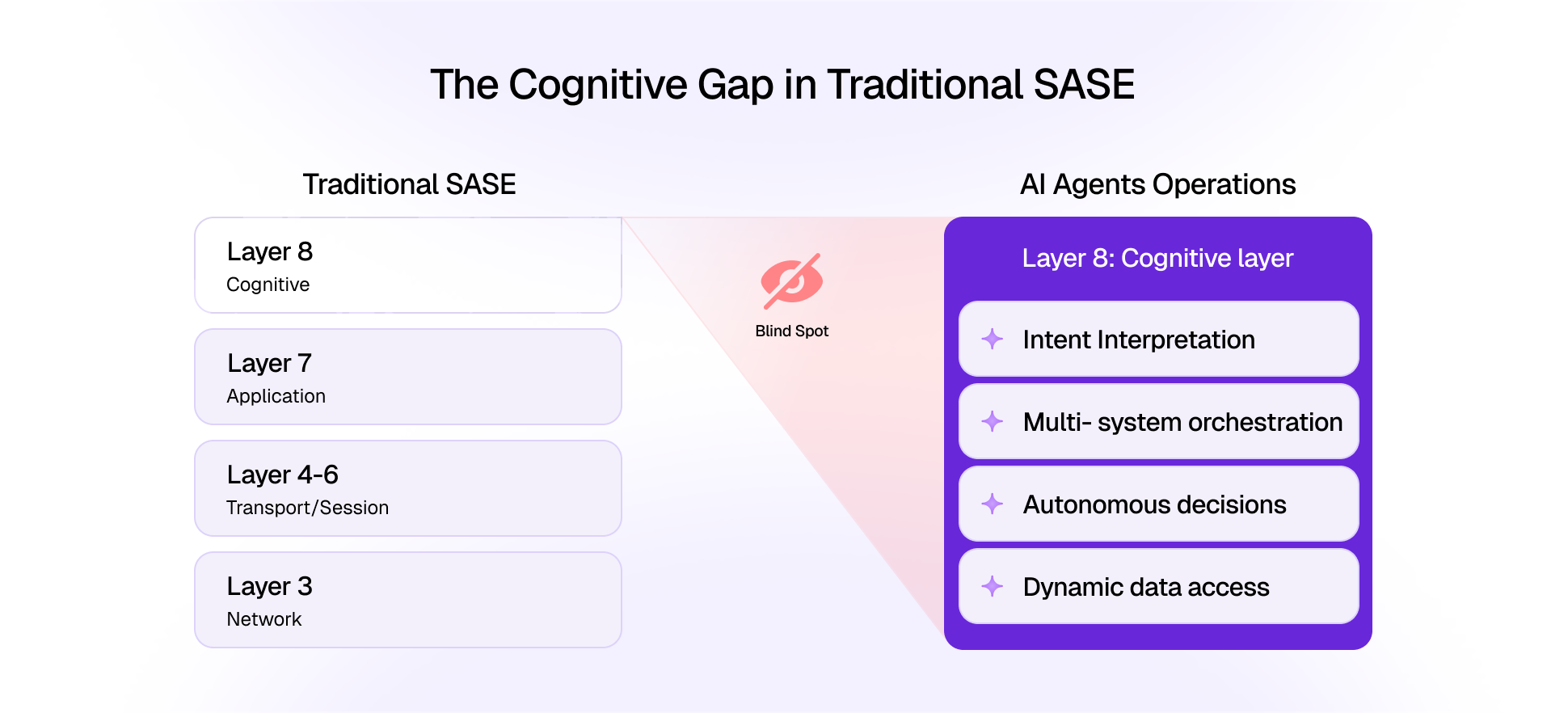
Emerging Threat Models Specific to Enterprise RAG
Embedding Inversion & Vector Database Attacks
Attackers can reconstruct sensitive original data from vector embeddings if they're not encrypted or adequately access-controlled. This vulnerability has been demonstrated in both open and private systems.
Index Poisoning
Malicious actors can insert or manipulate content in vector databases, resulting in out-of-policy or sensitive data leaks. Index poisoning is emerging as a significant RAG attack vector.
Transparency vs. Attack Surface
Displaying source documents for auditability can signal adversaries to the specific documents or knowledge base entries to target for poisoning or social engineering.
Industry Case Studies: Compliance and RAG
- Finance:
Banks use RAG for KYC/AML automation, where strict retrieval scoping and comprehensive audit logs are required to meet global regulatory requirements. - Healthcare:
Clinical RAG copilots are being deployed for patient support, but systems must prevent cross-patient leakage, limit PHI reconstruction from embeddings, and meet HIPAA’s access and minimization mandates. - Insurance & Legal:
For highly contextual and privileged documents, explainable outputs, policy-driven retrieval, and regular provenance audits are essential.
Encryption and Zero-Trust Architectures for RAG
- Encrypted Vector Stores:
Data should be protected at rest using AES-256 or attribute-based encryption. Choose hybrid or full encryption models based on risk sensitivity. - Zero Trust Everywhere:
Zero-trust architecture makes no implicit trust assumptions between users, system components, or processes, requiring continuous authentication and authorization with micro-segmentation to prevent lateral movement. - Data Anonymization:
Pseudonymize or anonymize sensitive content before indexing, and rigorously apply data minimization policies to align with global compliance requirements.
Privacy-Preserving Retrieval Techniques
- User-Isolated Knowledge Retrieval:
Cryptographic segmentation ensures users can only retrieve the documents they're authorized for, reducing accidental leakage. - Differential Privacy for Retrieval:
Add carefully tuned noise at the embedding or retrieval stage to defend against reconstruction attacks, as shown in recent privacy research. - Encrypted Retrieval Operations:
Employ homomorphic encryption and attribute-based keys so search and retrieval are done over encrypted data, strengthening privacy without manual decryption steps.
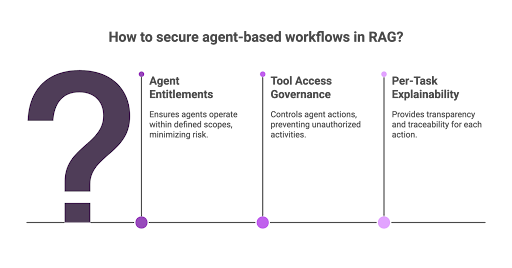
Secure Agent-Based Workflows in RAG
As enterprises transition to autonomous RAG agents and orchestration, securing agent action and output is critical.
- Agent Entitlements:
Each agent must be bound by explicit, minimal policy scopes, defining exactly what it may retrieve, access, and execute. - Tool Access Governance:
All agent tool calls, such as sending emails or transactions, must be strictly gated by both model output and policy engine logic. - Per-Task Explainability:
Each action or answer must be explainable and traceable to its triggering prompt and retrieved documents.
Best Practices and Implementation Checklist
Best Practices and Implementation Checklist
Auditing, Incident Response, and Ongoing Maintenance
Comprehensive Audit Trails
Log every user action, query, retrieval, filtering step, and model output with associated metadata and timestamps. Use immutably stored, encrypted logs as a foundation for regulatory compliance and incident analysis, following industry practices.
Incident Response Frameworks
Develop and maintain RAG-specific incident playbooks covering prompt injection detection and rollback, context poisoning mitigation, and precise tracing of unauthorized document access. Connect these playbooks to your organization’s broader SIEM/SOAR response system.
Continuous Security Testing
Regularly test your system using adversarial simulation tools. Integrate these into your CI/CD pipelines to maintain security with every data or model update.
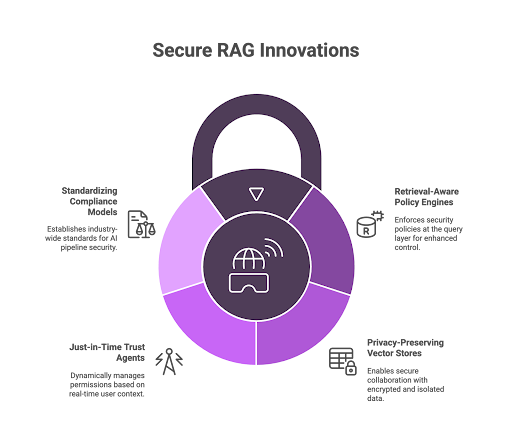
Future Innovations in Secure RAG
- Retrieval-Aware Policy Engines:
Next-gen security controls will enforce policy at the query layer, not just the application front end, as discussed in recent RAG security research. - Privacy-Preserving Vector Stores:
Federated and encrypted vector DB systems will enable secure, multi-party collaboration with strict isolation controls. - Just-in-Time Trust & Observability Agents:
Real-time trust management will dynamically adjust retrieval permissions and scope by user/session context and behavioral analytics. - Standardizing Compliance Models:
Industry and regulators are defining baseline requirements for traceability, explainability, and audit for generative AI pipelines.
Strategic Takeaways for Leaders
- Secure RAG is a layered architecture, requiring security at every step: embedding, indexing, retrieval, and generation, not just at the user interface.
- Regulated enterprises must apply to RAG the same risk and compliance rigor afforded to core, mission-critical information systems.
- The future of compliant enterprise AI will be driven by policy-aware agents, privacy-preserving infrastructure, and standardized, explainable auditing.
- Early and holistic investment in secure RAG will not only reduce operational and compliance risk, but also build the enterprise trust essential for responsible AI scaling.